Project Background | |
| Sector: Retail | Duration: 8 Weeks |
| Revenue: In excess of $100B | OSec Team Size: 4 |
| Footprint: Global | Test Areas: Cyber and Physical |
“Could we be destroyed by a cyber attack?”
This was the question posed by our client. Spoiler alert: It’s challenging for a single cyber attack to bring down a giant organization. Our experience shows that direct attacks on technology—such as a hack that brings down a system, data theft, or a ransomware attack—can cause damage, but the impact is usually not enough to bring a large organization to its knees.
Instead, technology often serves as a conduit to a larger outcome. That’s where the real damage occurs. A company that consistently fails its customers will suffer financially as those customers seek more trustworthy alternatives. This was the approach we took, and ultimately succeeded with, against one of the largest retailers in the world.
Approach
We began by speaking with stakeholders to determine what the impact of the attack would need to be to be considered catastrophic: a 10% revenue drop. We then worked to identify key business processes and review other relevant information. Over the course of 2 weeks information was analyzed, follow-up conversations were held and several high-impact scenarios were identified. The conclusion was an attack approach known as “Death by 1,000 cuts”.
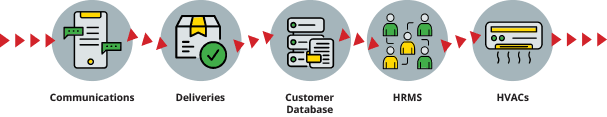
Death by 1,000 cuts involved a multi-pronged attack designed to erode customer confidence over time. Equipment across a range of stores (including refrigeration units and heating systems) could be disrupted, deliveries delayed, staff management systems compromised, internal communications accessed and the ability to send messages obtained. Key customer databases were also accessed and exfiltrated.
Because the engagement had a finite amount of time, the objective was to prove out that those target components could be breached. The customer database, HRMS, and communication systems were centralized. HVAC/Refrigeration and deliveries were standardized across all stores and distribution centers. Breaching even one component would be indicative that an attack could be executed at scale.
Attack Vectors
With 6 weeks remaining to determine if an attack was viable, the team chose three attack vectors:
- The management room in a store
- An Internet facing application
- A room at a vendor location
The client concluded that the potential for a breach via any of these vectors posed a significant risk. They were confident the the technical controls already in place and the security-awareness training provided to their staff significantly lowered the likelihood of a successful breach.
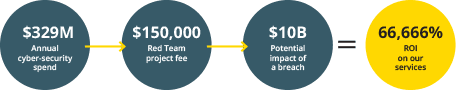
Regarding their technical controls, we were not given specific figures on the client’s security spending. However, according to Deloitte1, the average tech budget in 2023 was 5.49% of revenue, with cybersecurity expenditure typically accounting for 6-14% of IT budgets. For a company with $100B in total revenue, this translates to an approximate security allocation of $329M. Such an investment should provide sufficient protection to thwart any but the most well-funded nation-state attacks.
Initial Breach Attempts
Store Management Room Throughout the company’s physical locations, store management rooms were located at the back of stores, behind swing doors that had no access control. Various approaches were considered. The breach attempt we executed was as follows:
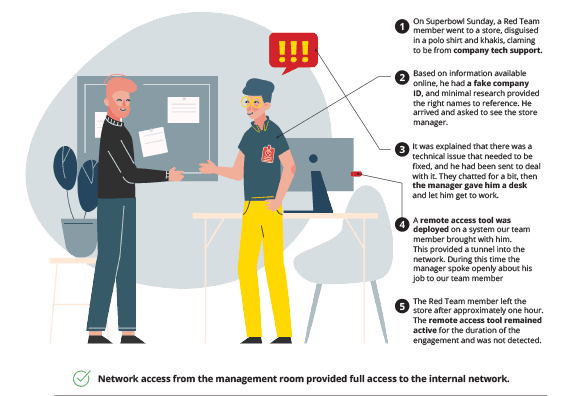
Vendor Room: The vendor room area selected was accessible from the street, and turnstiles were in place. However it was easy to tailgate (walk in right behind someone without swiping a key-card) and gain access to the area.
From there it was a simple task of finding an empty room and attempting to install a remote access system. Network connectivity into the internal network was confirmed and the system deployed. Since two remote access tools had been deployed, the decision was made to focus on the vendor room.
Application: One application was selected for testing. Despite various vectors being identified for possible exploitation. Given the time frame, these were scheduled for testing at a later date.
Trophy Achieved
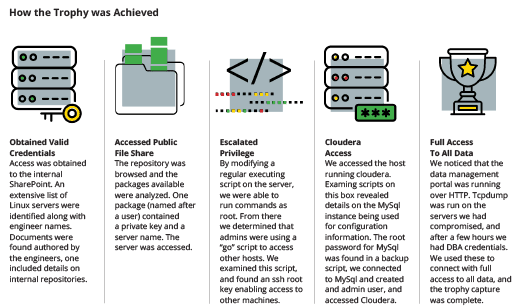
In 12 days, the project objectives were obtained with full access to the company’s global data analytics platform. Additionally the underlying Hadoop Cluster was accessed with full privileges, giving the OccamSec Red Team the ability to delete data, reconfigure the system, and conduct other administrator activities without being detected. No alerts were raised and all security controls were bypassed.
This took time to achieve. Because stealth was required, the team could not run any intrusive tests and considerable time was spent analyzing SharePoint for data and reviewing scripts and configuration information we were also able to obtain.
The Outcome
Systemic Issues: The project identified three core systemic issues the company needed to address. Tying these together is a misunderstanding of risk management, and possibly an over-reliance on compliance requirements as the final word in security.
It’s often conveyed that attackers only need to succeed once for a major impact; this is a disservice to both attackers and defenders. One vulnerability alone is probably not going to destroy a business’s revenue operations. A collection of them, with an attacker who is focused on that high-impact outcome presents a risk-management issue that requires a holistic assessment of the organizational operations, not just technical support systems.
- Lack of security awareness. Confidential data is being stored in all-employee accessible SharePoint files. While security-awareness training is a compliance requirement for many, our experience proves it provides any major value. Technical controls which remove the potential for human error have a far better chance of success. Posters and a PowerPoint session will not override basic human instincts.
- Security programs not built on high-impact business outcomes. As is often the case, the program was developed with little to no consideration of business impact. How does the organization generate revenue? What cyber attack impacts would cause the most harm? These questions had not been initially asked of the leadership teams. Instead, a standard defensive in-depth playbook was used, which can be successful when its deployed around impact. Looking to just secure everything, everywhere, and monitor everything is a recipe for disaster for most organizations.
- Lack of the realization that cyber security risk is constantly changing. An annual penetration test against specific applications may work. Given the cadence with which new vulnerabilities are discovered it is more likely that systems are exposed for long periods of time. It also needs to be understood that vulnerabilities can be chained together across both technical and non-technical targets.The ability to access a supposedly secure area may not amount to much on its own. But that combined with poor control over network access points, a flat network structure, confidential information being stored in SharePoint files, and monitoring controls not based on actual attacks, is a recipe for disaster.
Return on Investment
Returning to the attack vectors section and the budget numbers, this project provides an accurate measure of the return on investment since the trophy was considered—by the business—to have a material impact on revenue. When executed with precision and focused on specific business impacts, Red Teaming can reveal critical vulnerabilities that should be addressed to maintain customer trust and business growth.